
it-sa 2025 in Nuremberg is over — and it was a resounding success. Three intense days focused on cybersecurity, compliance, and IT integration are now behind us. For us, the trade fair was not only an opportunity to present our solutions live, but above all a place for professional exchange, inspiration, and encounters.
it-sa – Home of Security – Europe’s leading trade fair for IT security
it-sa is considered Europe’s leading trade fair for IT security. Every year, it attracts thousands of experts from business, government, and research. The focus is on current topics such as cyber defense, data protection, risk and compliance management, and the challenges of modern IT infrastructures. In addition to the exhibitor stands, forums, specialist presentations, and discussion panels offer practical insights into the trends and technologies that are shaping the security landscape.
Once again this year, the trade fair in Nuremberg was a central meeting place for the security community—and we were right in the middle of it.




IT documentation, attack detection, and integration combined
Our booth in Hall 7 was well attended throughout the entire trade fair. Interest focused primarily on one topic: How can IT security be designed today to function in an integrated, transparent, and automated manner?
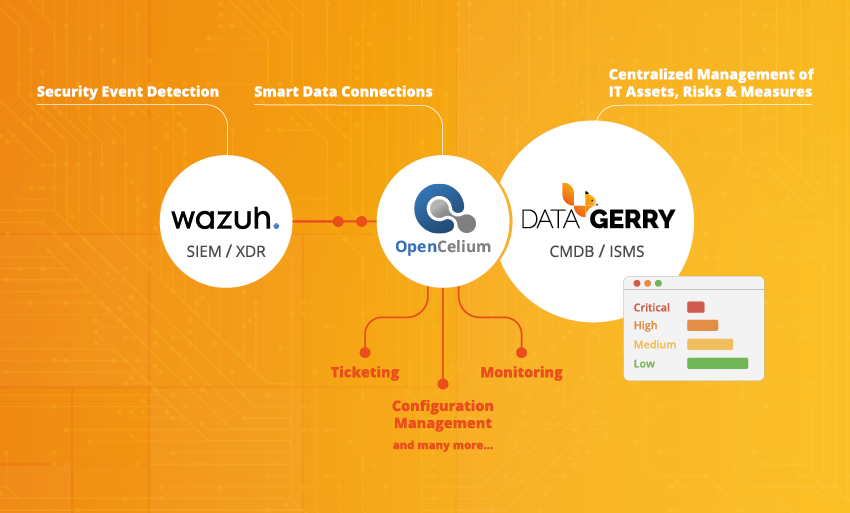
Our answer: With the combination of DataGerry, Wazuh, and OpenCelium — an open, flexible solution that combines documentation, attack detection, and API integration.

DataGerry: Central IT documentation and ISMS
DataGerry is our open source CMDB (Configuration Management Database), which goes far beyond traditional IT documentation. It maps all relevant IT assets in a structured manner—from servers and applications to networks — and makes this information available centrally. In addition, DataGerry can be used as an ISMS (Information Security Management System). This provides companies with a flexible platform for mapping and controlling processes, responsibilities, and security measures in accordance with NIS2 or ISO 27001 requirements.

Wazuh: Attack detection and security monitoring
Wazuh adds an operational security layer to DataGerry. The open source security platform monitors systems, analyzes log data, and detects security-related events in real time. Through integration with DataGerry, this information flows directly into the documentation, making attacks or vulnerabilities visible in context and traceable.
This aspect is particularly crucial in the context of the NIS2 directive: Companies must not only document their IT assets, but also be able to detect, evaluate, and verify security incidents.
Wazuh provides the technical basis for adequate attack detection, as expressly required by NIS2 – especially for critical infrastructure companies or organizations that have taken out cyber insurance.
Continuous monitoring and automatic alerts help to shorten response times and provide audit-proof security evidence at all times.

OpenCelium: Open Source API Integration
The third component is OpenCelium – an API integration platform. It connects DataGerry, Wazuh, and other applications within the company via standardized interfaces. This allows security-related data to be automatically exchanged, enriched, and processed – without manual intervention.
The result is a seamless flow of information:
- Events from Wazuh are automatically transferred to DataGerry.
- CMDB data can be transferred to external tools or linked to SIEM systems.
- Changes or status information are synchronized.
This integration creates transparency and efficiency while reducing the risk of human error. For companies that need to implement NIS2 requirements, this creates a comprehensive security architecture that combines documentation, attack detection, and integration on a single platform.
NIS2 in practice: A one-stop solution for security and compliance
One of the highlights of the trade fair was our presentation “Implementing NIS2 with DataGerry – CMDB, ISMS & attack detection as a one-stop solution.” Our expert Kai Schubert-Altmann showed how companies can use this combination to master the balancing act between compliance and operational security.
The requirements of the EU NIS2 Directive are clear: companies must know their IT assets, assess risks, document security measures, and make security incidents traceable.
With DataGerry, Wazuh, and OpenCelium, this process can be mapped completely digitally:
- Documentation & transparency: All systems, dependencies, and responsibilities are centrally recorded in the CMDB.
- Attack detection: Security events are automatically detected, documented, and evaluated—a central component of NIS2 compliance.
- Integration: OpenCelium integrates information from other tools to create a complete security ecosystem.
This solution is not only technically elegant, but also economically sensible – especially for organizations that want to rely on open, scalable systems.
More tips on the practical implementation of the NIS2 directive in our free checklist
Dialogue, practical relevance, and new ideas
In addition to the technical topics, the trade fair was above all one thing: a place for exchange. Whether it was about CMDB strategies, attack detection, or API integration, the discussions at our booth showed how great the need is for practical, open solutions.
The positive response and interest in DataGerry, Wazuh, and OpenCelium confirm our decision to continue on this path.
We were also particularly pleased to see our partners from the i-doit Group, KIX, LOGINventory, and Sumo Logic again. Every year, it-sa offers an excellent opportunity to nurture existing partnerships, exchange ideas, and gain new inspiration from the community.
For us, the personal contact with customers, partners, and interested parties was a valuable experience. We will continue many of the discussions in the coming weeks – with new ideas, perspectives, and concrete solutions.
Conclusion: Three successful days full of energy and inspiration
For us, it-sa 2025 was more than just a trade fair—it was an intensive insight into the current challenges and opportunities in the world of IT security.
A big thank you goes out to all visitors, partners, and colleagues who made these three days a real highlight.
We are already looking forward to it-sa 2026 – and to continuing the dialogue on secure, integrated, and open IT systems.







Contact
Do you have any questions, suggestions, requests, or are you facing a particular challenge? We look forward to hearing from you!
+49 (0) 89 608668-0


